Which task is unavailable for administrative accounts that authenticate using RSA SecurID Authentication?
A. reset forgotten passwords
B. import organizational units (OU) from Active Directory
C. configure external logging
D. enable Session Based Authentication with Web Services
Which two Symantec Endpoint Protection components are used to distribute content updates? (Select two.)
A. Group Update Provider (GUP)
B. Shared Insight Cache Server
C. Symantec Protection Center
D. Symantec Endpoint Protection Manager
E. Symantec Insight Database
What is a supported migration path for Symantec Endpoint Protection?
A. Symantec Endpoint Protection Enterprise Edition 12.1 > Symantec Endpoint Protection Small Business Edition 12.1
B. Symantec Endpoint Protection Small Business Edition 12.1 > Symantec Endpoint Protection Enterprise Edition 12.1
C. Symantec Endpoint Protection 12.1 Enterprise Edition > Symantec Endpoint Protection 11.x Enterprise Edition
D. Symantec Endpoint Protection Small Business Edition 12.1 > Symantec Endpoint Protection 11.x Small Business Edition
A company has 10,000 Symantec Endpoint Protection (SEP) clients deployed using two Symantec Endpoint Protection Managers (SEPMs).
Which configuration is recommended to ensure that each SEPM is able to effectively handle the communications load with the SEP clients?
A. Push mode
B. Client control mode
C. Server control mode
D. Pull mode
Which action does the Shared Insight Cache (SIC) server take when the whitelist reaches maximum capacity?
A. The SIC server allocates additional memory for the whitelist as needed.
B. The SIC server will start writing the cache to disk.
C. The SIC server will remove the least recently used items based on the prune size.
D. The SIC server will remove items with the fewest number of votes.
Why does Power Eraser need Internet access?
A. to leverage Symantec Insight
B. to validate root certificates on all portable executables (PXE) files
C. to ensure the Power Eraser tool is the latest release
D. to look up CVE vulnerabilities
Which action does SONAR take before convicting a process?
A. quarantines the process
B. blocks suspicious behavior
C. reboots the system
D. checks the reputation of the process
Refer to the exhibit.
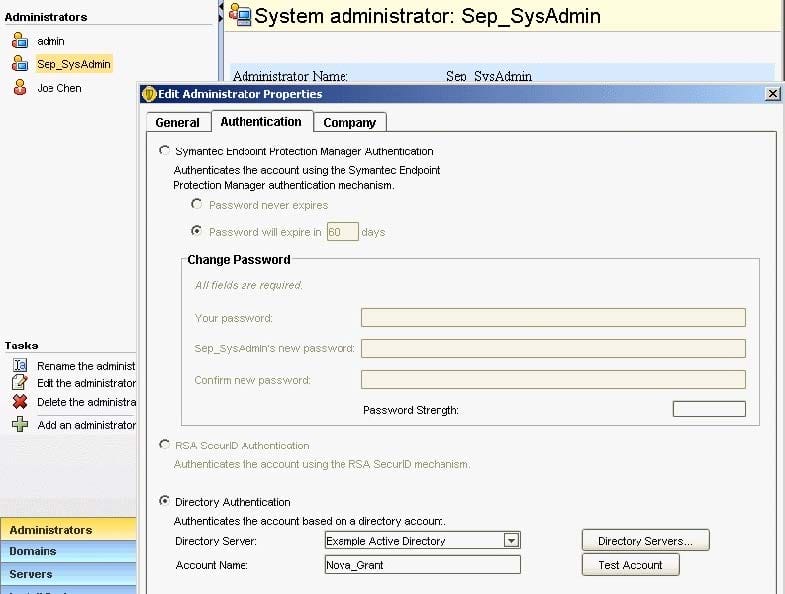
An administrator has configured the Symantec Endpoint Protection Manager (SEPM) to use Active Directory authentication. The administrator defines a new Symantec Endpoint Protection administrator named Sep_SysAdmin, configured to use Directory Authentication.
Which password needs to be entered when the administrator logs in to the SEPM console as Sep_SysAdmin?
A. The password for the Active Directory account Nova_Grant
B. The password for the SEPM account Nova_Grant
C. The password for the Active Directory account Sep_SysAdmin
D. The password for the SEPM account Sep_SysAdmin
How should an administrator set up an alert to be notified when manual remediation is needed on an endpoint?
A. Add a System event notification and specify "Left Alone" for the action taken. Choose to log the notification and send an e-mail to the system administrators
B. Add a Single Risk Event notification and specify "Left Alone" for the action taken. Choose to log the notification and send an e-mail to the system administrators
C. Add a New risk detected notification and specify "Left Alone" for the action taken. Choose to log the notification and send an e-mail to the system administrators
D. Add a Client security alert notification and specify "Left Alone" for the action taken. Choose to log the notification and send an e-mail to the system administrators
An organization needs to add a collection of DNS host names to permit in the firewall policy.
How should the SEP Administrator add these DNS host names as a single rule in the firewall policy?
A. Create a Host Group and add the DNS domain. Then create a firewall rule with the new Host Group as the Source/Destination
B. Create a Host Group and add the DNS host names. Then create a firewall rule with the new Host Group as the Source/Destination
C. Create a Host Group and add the DNS host names. Then create a firewall rule with the new Host Group as the Local/Remote
D. Create a Host Group and add the DNS domain. Then create a firewall rule with the new Host Group as the Local/Remote