If you perform a port scan with a TCP ACK packet, what should an OPEN port return?
A. RST
B. No Reply
C. SYN/ACK
D. FIN
Lee is using Wireshark to log traffic on his network. He notices a number of packets being directed to an internal IP from an outside IP where the packets are ICMP and their size is around 65,536 bytes. What is Lee seeing here?
A. Lee is seeing activity indicative of a Smurf attack.
B. Most likely, the ICMP packets are being sent in this manner to attempt IP spoofing.
C. Lee is seeing a Ping of death attack.
D. This is not unusual traffic, ICMP packets can be of any size.
Charlie is the network administrator for his company. Charlie just received a new Cisco router and wants to test its capabilities out and to see if it might be susceptible to a DoS attack resulting in its locking up. The IP address of the Cisco switch is 172.16.0.45. What command can Charlie use to attempt this task?
A. Charlie can use the command: ping -l 56550 172.16.0.45 -t.
B. Charlie can try using the command: ping 56550 172.16.0.45.
C. By using the command ping 172.16.0.45 Charlie would be able to lockup the router
D. He could use the command: ping -4 56550 172.16.0.45.
You are trying to hijack a telnet session from a victim machine with IP address 10.0.0.5 to Cisco router at 10.0.0.1. You sniff the traffic and attempt to predict the sequence and acknowledgement numbers to successfully hijack the telnet session.
Here is the captured data in tcpdump.
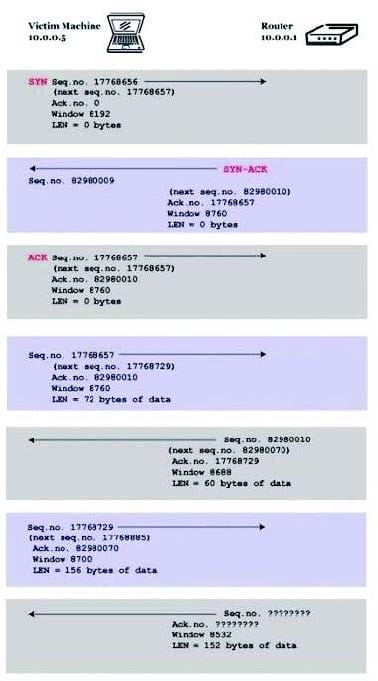
What are the next sequence and acknowledgement numbers that the router will send to the victim machine?
A. Sequence number: 82980070 Acknowledgement number: 17768885A.
B. Sequence number: 17768729 Acknowledgement number: 82980070B.
C. Sequence number: 87000070 Acknowledgement number: 85320085C.
D. Sequence number: 82980010 Acknowledgement number: 17768885D.
#define MAKE_STR_FROM_RET(x) ((x)and0xff), (((x)and0xff00)8), (((x)and0xff0000)16), (((x)and0xff000000)24) char infin_loop[]=
/* for testing purposes */
"\xEB\xFE";
char bsdcode[] =
/* Lam3rZ chroot() code rewritten for FreeBSD by venglin */ "\x31\xc0\x50\x50\x50\xb0\x7e\xcd\x80\x31\xdb\x31\xc0\x43" "\x43\x53\x4b\x53\x53\xb0\x5a\xcd\x80 \xeb\x77\x5e\x31\xc0" "\x8d\x5e\x01\x88\x46\x04\x66\x68\xff\xff\x01\x53\x53
\xb0" "\x88\xcd\x80\x31\xc0\x8d\x5e\x01\x53\x53\xb0\x3d\xcd\x80" "\x31\xc0\x31\xdb \x8d\x5e\x08\x89\x43\x02\x31\xc9\xfe\xc9" "\x31\xc0\x8d\x5e\x08\x53\x53\xb0\x0c\xcd\x80\xfe\xc9\x75" "\xf1\x31\xc0\x88\x46\x09\x8d\x5e\x08\x53\x53\xb0
\x3d \xcd" "\x80\xfe\x0e\xb0\x30\xfe\xc8\x88\x46\x04\x31\xc0\x88\x46" "\x07\x89\x76\x08\x89\x46\x0c\x89\xf3\x8d\x4e\x08\x8d\x56" "\x0c\x52\x51\x53\x53\xb0\x3b\xcd \x80\x31\xc0\x31\xdb\x53" "\x53\xb0\x01\xcd\x80\xe8\x84\xff\xff\xff\xff\x01
\xff\xff\x30" "\x62\x69\x6e\x30\x73\x68\x31\x2e\x2e\x31\x31\x76\x65\x6e" "\x67\x6c\x69 \x6e";static int magic[MAX_MAGIC],magic_d[MAX_MAGIC]; static char *magic_str=NULL;
int before_len=0;
char *target=NULL, *username="user", *password=NULL;
struct targets getit;
The following exploit code is extracted from what kind of attack?
A. Remote password cracking attack
B. SQL Injection
C. Distributed Denial of Service
D. Cross Site Scripting
E. Buffer Overflow
You have performed the traceroute below and notice that hops 19 and 20 both show the same IP address.
What can be inferred from this output?
1 172.16.1.254 (172.16.1.254) 0.724 ms 3.285 ms 0.613 ms 2 ip68-98-176-1.nv.nv.cox.net (68.98.176.1) 12.169 ms 14.958 ms 13.416 ms 3 ip68-98-176- 1.nv.nv.cox.net (68.98.176.1) 13.948 ms ip68-100-0-1.nv.nv.cox.net (68.100.0.1)
16.743
ms 16.207 ms 4 ip68-100-0-137.nv.nv.cox.net (68.100.0.137) 17.324 ms 12.933 ms 20.938 ms 5 68.1.1.4 (68.1.1.4) 12.439 ms 220.166 ms 204.170 ms 6 so-6-0-0.gar2.wdc1.Level3.net (67.29.170.1) 16.177 ms 25.943 ms 14.104 ms 7 unknown.Level3.net (209.247.9.173) 14.227 ms 17.553 ms 15.415 ms 8 so-0-1- 0.bbr1.NewYork1.level3.net (64.159.1.41) 17.063 ms 20.960 ms 19.512 ms 9 so-7-0-0-gar1.NewYork1.Level3.net (64.159.1.182) 20.334 ms 19.440 ms
17.938
ms 10 so-4-0-0.edge1.NewYork1.Level3.net (209.244.17.74) 27.526 ms 18.317 ms 21.202 ms 11 uunet-level3-oc48.NewYork1.Level3.net (209.244.160.12) 21.411 ms 19.133 ms 18.830 ms 12 0.so-6-0-0.XL1.NYC4.ALTER.NET
(152.63.21.78)
21.203 ms 22.670 ms 20.11 ms 13 0.so-2-0-0.TL1.NYC8.ALTER.NET (152.63.0.153) 30.929 ms 24.858 ms 23.108 ms 14 0.so-4-1-0.TL1.ATL5.ALTER.NET (152.63.10.129) 38.894 ms 33.244 33.910 ms 15 0.so-7-00.XL1.MIA4.ALTER.NET (152.63.86.189) 51.165 ms 49.935 ms 49.466 ms 16 0.so-3-0-0.XR1.MIA4.ALTER.NET (152.63.101.41) 50.937 ms 49.005 ms 51.055 ms 17 117.ATM6-0.GW5.MIA1.ALTER.NET (152.63.82.73) 51.897 ms 50.280 ms 53.647 ms 18 example-gwl.customer.alter.net (65.195.239.14) 51.921 ms 51.571 ms 56.855 ms 19 www.ABC.com (65.195.239.22) 52.191 ms 52.571 ms 56.855 ms 20 www.ABC.com (65.195.239.22) 53.561 ms 54.121 ms 58.333 ms
A.
An application proxy firewall
B.
A stateful inspection firewall
C.
A host based IDS
D.
A Honeypot
How would you prevent session hijacking attacks?
A. Using biometrics access tokens secures sessions against hijacking
B. Using non-Internet protocols like http secures sessions against hijacking
C. Using hardware-based authentication secures sessions against hijacking
D. Using unpredictable sequence numbers secures sessions against hijacking
What type of port scan is shown below?
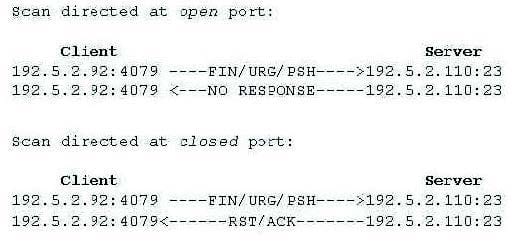
A. Idle Scan
B. Windows Scan
C. XMAS Scan
D. SYN Stealth Scan
Why would an attacker want to perform a scan on port 137?
A. To discover proxy servers on a network
B. To disrupt the NetBIOS SMB service on the target host
C. To check for file and print sharing on Windows systems
D. To discover information about a target host using NBTSTAT
A very useful resource for passively gathering information about a target company is:
A. Host scanning
B. Whois search
C. Traceroute
D. Ping sweep