Drag and drop the appropriate principle documents in front of their respective functions.
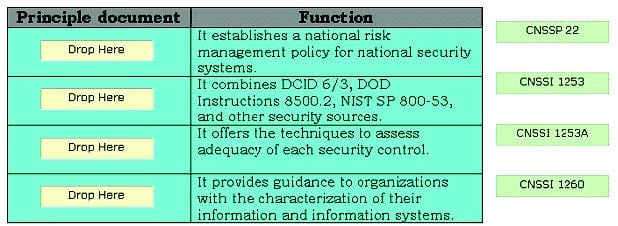
Select and Place:

You work as a project manager for BlueWell Inc. You are working on a project and the management wants a rapid and cost-effective means for establishing priorities for planning risk responses in your project. Which risk management process can satisfy management's objective for your project?
A. Qualitative risk analysis
B. Historical information
C. Rolling wave planning
D. Quantitative analysis
Which of the following are the levels of public or commercial data classification system? Each correct answer represents a complete solution. Choose all that apply.
A. Sensitive
B. Private
C. Unclassified
D. Confidential
E. Secret
F. Public
Which of the following vulnerabilities occurs when an application directly uses or concatenates potentially hostile input with data file or stream functions?
A. Insecure cryptographic storage
B. Malicious file execution
C. Insecure communication
D. Injection flaw
Which of the following terms refers to a mechanism which proves that the sender really sent a particular message?
A. Confidentiality
B. Non-repudiation
C. Authentication
D. Integrity
Which of the following refers to the ability to ensure that the data is not modified or tampered with?
A. Integrity
B. Availability
C. Non-repudiation
D. Confidentiality
The Chief Information Officer (CIO), or Information Technology (IT) director, is a job title commonly given to the most senior executive in an enterprise. What are the responsibilities of a Chief Information Officer? Each correct answer represents a complete solution. Choose all that apply.
A. Facilitating the sharing of security risk-related information among authorizing officials
B. Preserving high-level communications and working group relationships in an organization
C. Establishing effective continuous monitoring program for the organization
D. Proposing the information technology needed by an enterprise to achieve its goals and then working within a budget to implement the plan
Which of the following approaches can be used to build a security program? Each correct answer represents a complete solution. Choose all that apply.
A. Right-Up Approach
B. Left-Up Approach
C. Top-Down Approach
D. Bottom-Up Approach
According to the NIST SAMATE, dynamic analysis tools operate by generating runtime vulnerability scenario using some functions. Which of the following are functions that are used by the dynamic analysis tools and are summarized in the NIST SAMATE? Each correct answer represents a complete solution. Choose all that apply.
A. Implementation attack
B. Source code security
C. File corruption
D. Network fault injection
A Web-based credit card company had collected financial and personal details of Mark before issuing him a credit card. The company has now provided Mark's financial and personal details to another company. Which of the following Internet laws has the credit card issuing company violated?
A. Trademark law
B. Security law
C. Privacy law
D. Copyright law