While looking through the IIS log file of a web server, you find the following entries:
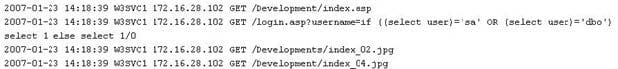
What is evident from this log file?
A. Web bugs
B. Cross site scripting
C. Hidden fields
D. SQL injection is possible
What type of attack sends spoofed UDP packets (instead of ping packets) with a fake source address to the IP broadcast address of a large network?
A. Fraggle
B. Smurf scan
C. SYN flood
D. Teardrop
The newer Macintosh Operating System is based on: A. OS/2
B. BSD Unix
C. Linux
D. Microsoft Windows
In a FAT32 system, a 123 KB file will use how many sectors?
A. 34
B. 25
C. 11
D. 56
When investigating a network that uses DHCP to assign IP addresses, where would you look to determine which system (MAC address) had a specific IP address at a specific time?
A. on the individual computer's ARP cache
B. in the Web Server log files
C. in the DHCP Server log files
D. there is no way to determine the specific IP address
While working for a prosecutor, what do you think you should do if the evidence you found appears to be exculpatory and is not being released to the defense?
A. Keep the information of file for later review
B. Destroy the evidence
C. Bring the information to the attention of the prosecutor, his or her supervisor or finally to the judge
D. Present the evidence to the defense attorney
Printing under a Windows Computer normally requires which one of the following files types to be created?
A. EME
B. MEM
C. EMF
D. CME
The police believe that Melvin Matthew has been obtaining unauthorized access to computers belonging to numerous computer software and computer operating systems manufacturers, cellular telephone manufacturers, Internet Service Providers and Educational Institutions. They also suspect that he has been stealing, copying and misappropriating proprietary computer software belonging to the several victim companies. What is preventing the police from breaking down the suspects door and searching his home and seizing all of his computer equipment if they have not yet obtained a warrant?
A. The Fourth Amendment
B. The USA patriot Act
C. The Good Samaritan Laws
D. The Federal Rules of Evidence
When cataloging digital evidence, the primary goal is to
A. Make bit-stream images of all hard drives
B. Preserve evidence integrity
C. Not remove the evidence from the scene
D. Not allow the computer to be turned off
Microsoft Outlook maintains email messages in a proprietary format in what type of file?
A. .email
B. .mail
C. .pst
D. .doc