An executive has decided to move a company's customer-facing application to the cloud after experiencing a lengthy power outage at a locally managed service provider's data center. The executive would like a solution that can be implemented as soon as possible. Which of the following will BEST prevent similar issues when the service is running in the cloud? (Choose two.)
A. Placing the application instances in different availability zones
B. Restoring the snapshot and starting the new application instance from a different zone
C. Enabling autoscaling based on application instance usage
D. Having several application instances running in different VPCs
E. Using the combination of block storage and multiple CDNs in each application instance
F. Setting up application instances in multiple regions
A local university that has a global footprint is undertaking a complete overhaul of its website and associated systems Some of the requirements are:
1.
Handle an increase in customer demand of resources
2.
Provide quick and easy access to information
3.
Provide high-quality streaming media
4.
Create a user-friendly interface
Which of the following actions should be taken FIRST?
A. Deploy high-availability web servers.
B. Enhance network access controls.
C. Implement a content delivery network.
D. Migrate to a virtualized environment.
A bank hired a security architect to improve its security measures against the latest threats. The solution must meet the following requirements:
1.
Recognize and block fake websites.
2.
Decrypt and scan encrypted traffic on standard and non-standard ports.
3.
Use multiple engines for detection and prevention.
4.
Have central reporting.
Which of the following is the BEST solution the security architect can propose?
A. CASB
B. Web filtering
C. NGFW
D. EDR
The Chief information Officer (CIO) of a large bank, which uses multiple third-party organizations to deliver a service, is concerned about the handling and security of customer data by the parties.
Which of the following should be implemented to BEST manage the risk?
A. Establish a review committee that assesses the importance of suppliers and ranks them according to contract renewals. At the time of contract renewal, incorporate designs and operational controls into the contracts and a right-to-audit clause. Regularly assess the supplier's post-contract renewal with a dedicated risk management team.
B. Establish a team using members from first line risk, the business unit, and vendor management to assess only design security controls of all suppliers. Store findings from the reviews in a database for all other business units and risk teams to reference.
C. Establish an audit program that regularly reviews all suppliers regardless of the data they access, how they access the data, and the type of data, Review all design and operational controls based on best practice standard and report the finding back to upper management.
D. Establish a governance program that rates suppliers based on their access to data, the type of data, and how they access the data Assign key controls that are reviewed and managed based on the supplier's rating. Report finding units that rely on the suppliers and the various risk teams.
The Chief Information Officer (CIO) wants to establish a non-binding agreement with a third party that outlines the objectives of the mutual arrangement dealing with data transfers between both organizations before establishing a formal partnership. Which of the following would MOST likely be used?
A. MOU
B. OLA
C. NDA
D. SLA
A security tester is performing a black-box assessment of an RFID access control system. The tester has a handful of RFID tags and is able to access the reader. However the tester cannot disassemble the reader because it is in use by the
company.
Which of the following shows the steps the tester should take to assess the RFID access control system in the correct order?
A. 1 Attempt to eavesdrop and replay RFID communications.
2.
Determine the protocols being used between the tag and the reader.
3.
Retrieve the RFID tag identifier and manufacturer details.
4.
Take apart an RFID tag and analyze the chip.
B. 1. Determine the protocols being used between the tag and the reader.
2.
Take apart an RFID tag and analyze the chip.
3.
Retrieve the RFID tag identifier and manufacturer details.
4.
Attempt to eavesdrop and replay RFID communications.
C. 1. Retrieve the RFID tag identifier and manufacturer details.
2. Determine the protocols is being used between the tag and the reader.
3 Attempt to eavesdrop and replay RFID communications.
4. Take apart an RFID tag and analyze the chip.
D. 1 Take apart an RFID tag and analyze the chip.
2.
Retrieve the RFID tag identifier and manufacturer details.
3.
Determine the protocols being used between the tag and the reader.
4.
Attempt to eavesdrop and replay RFID communications.
A Chief information Security Officer (CISO) is developing corrective-action plans based on the following from a vulnerability scan of internal hosts:
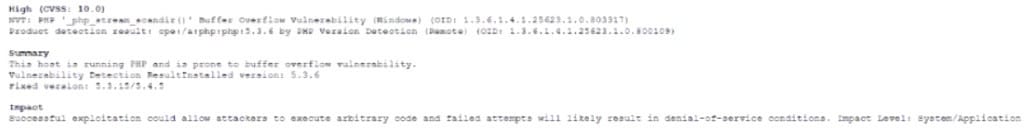
Which of the following MOST appropriate corrective action to document for this finding?
A. The product owner should perform a business impact assessment regarding the ability to implement a WAF.
B. The application developer should use a static code analysis tool to ensure any application code is not vulnerable to buffer overflows.
C. The system administrator should evaluate dependencies and perform upgrade as necessary.
D. The security operations center should develop a custom IDS rule to prevent attacks buffer overflows against this server.
A software company wants to build a platform by integrating with another company's established product. Which of the following provisions would be MOST important to include when drafting an agreement between the two companies?
A. Data sovereignty
B. Shared responsibility
C. Source code escrow
D. Safe harbor considerations
An organization developed a social media application that is used by customers in multiple remote geographic locations around the world. The organization's headquarters and only datacenter are located in New York City. The Chief Information Security Officer wants to ensure the following requirements are met for the social media application:
1.
Low latency for all mobile users to improve the users' experience
2.
SSL offloading to improve web server performance
3.
Protection against DoS and DDoS attacks
4.
High availability
Which of the following should the organization implement to BEST ensure all requirements are met?
A. A cache server farm in its datacenter
B. A load-balanced group of reverse proxy servers with SSL acceleration
C. A CDN with the origin set to its datacenter
D. Dual gigabit-speed Internet connections with managed DDoS prevention
Which of the following is required for an organization to meet the ISO 27018 standard?
A. All Pll must be encrypted.
B. All network traffic must be inspected.
C. GDPR equivalent standards must be met
D. COBIT equivalent standards must be met