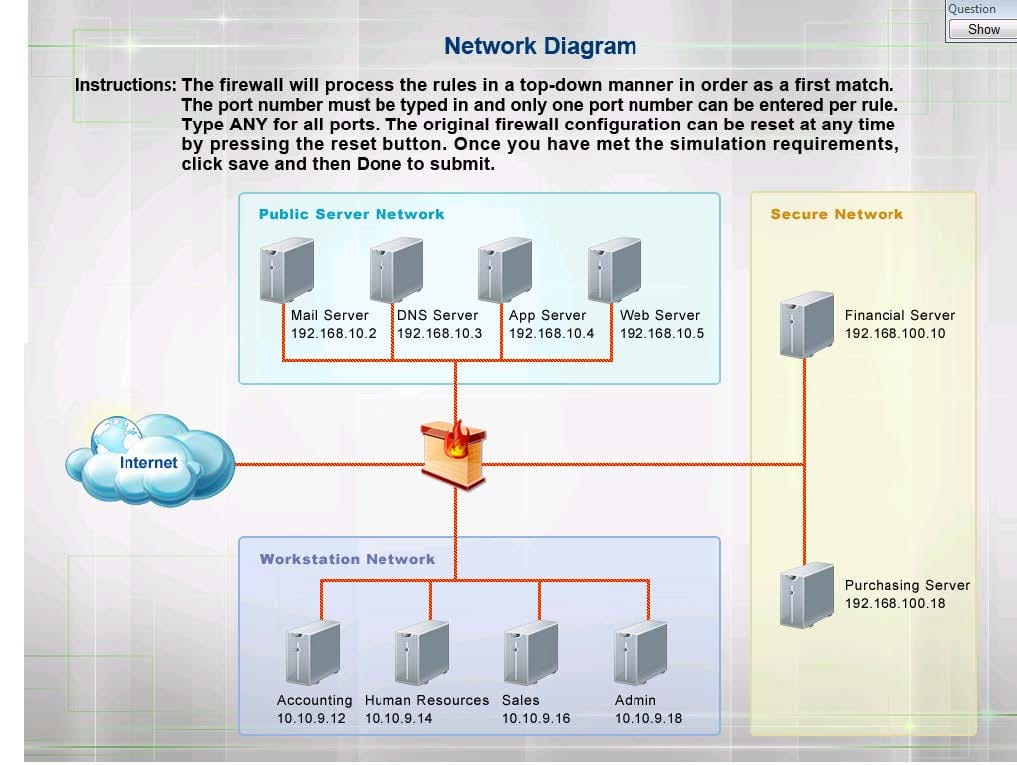
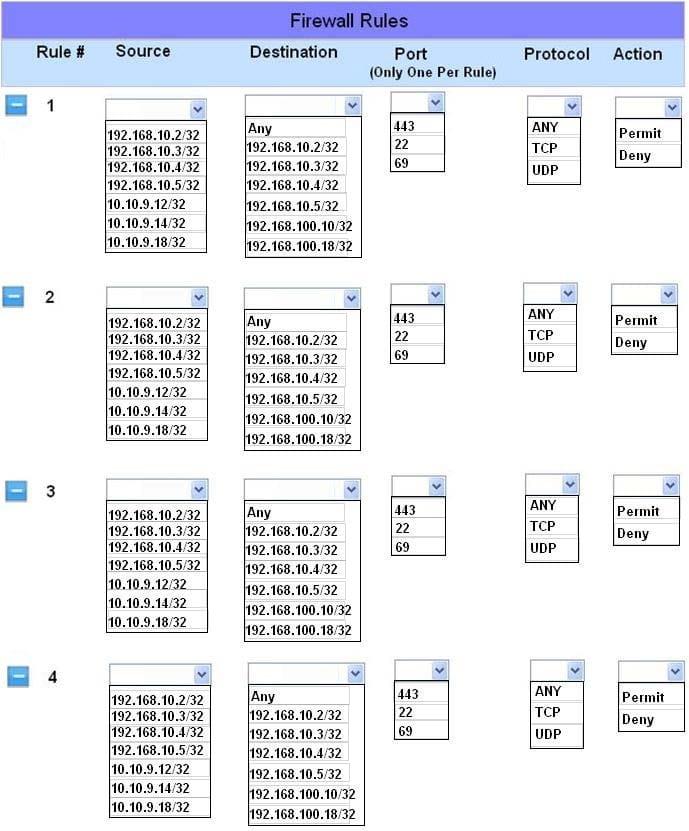
The security administrator has installed a new firewall which implements an implicit DENY policy by default. Click on the firewall and configure it to allow ONLY the following communication.
1.
The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2.
The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3.
The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can
be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.
Hot Area:
An audit found that an organization needs to implement job rotation to be compliant with regulatory requirements. To prevent unauthorized access to systems after an individual changes roles or departments, which of the following should the organization implement?
A. Permission auditing and review
B. Exit interviews
C. Offboarding
D. Multifactor authentication
A computer forensics team is performing an integrity check on key systems files. The team is comparing the signatures of original baseline les with the latest signatures. The original baseline was taken on March 2, 2016. and was established to be clean of malware and uncorrupted. The latest tile signatures were generated yesterday. One file is known to be corrupted, but when the team compares the signatures of the original and latest ies, the team sees the Following:
Original: 2d da b1 4a fc f1 98 06 b1 e5 26 b2 df e5 5b 3e cb 83 e1
Latest: 2d da b1 4a 98 fc f1 98 bl e5 26 b2 df e5 5b 3e cb 83 e1
Which of the following is MOST likely the situation?
A. The forensics team must have reverted the system to the original date. Which resulted in an identical hash calculation?
B. The original baseline was compromised, so the corrupted le was always on the system.
C. The signature comparison is using two different algorithms that happen to have generated the same values.
D. The algorithm used to calculate the hash has a collision weakness, and an attacker has exploited it.
A security analyst received an after-hours alert indicating that a large number of accounts with the suffix "admin'' were locked out. The accounts were all locked out after five unsuccessful login attempts, and no other accounts on the network triggered the same alert. Which of the following is the BEST explanation for these alerts?
A. The standard naming convention makes administrator accounts easy to identify, and they were targeted for an attack.
B. The administrator accounts do not have rigid password complexity rules, and this made them easier to crack.
C. The company has implemented time-of-day restrictions, and this triggered a false positive alert when the administrators tried to log in
D. The threshold for locking out administrator accounts is too high, and it should be changed from five to three to prevent unauthorized access attempts.
When choosing a hashing algorithm for storing passwords in a web server database, which of the following is the BEST explanation for choosing HMAC-MD5 over simple MD5?
A. HMAC provides hardware acceleration thus speeding up authentication
B. HMAC adds a transport layer handshake which improves authentication
C. HMAC-MD5 can be decrypted taster speeding up performance
D. HMAC-M05 is more resistant to brute forcing
A security engineer is configuring a wireless network that must support mutual authentication of the wireless client and the authentication server before users provide credentials. The wireless network must also support authentication with usernames and passwords.
Which of the following authentication protocols MUST the security engineer select?
A. EAP-FAST
B. EAP-TLS
C. PEAP
D. EAP
A systems administrator wants to configure an enterprise wireless solution that supports authentication over HTTPS and wireless encryption using AES. Which of the following should the administrator configure to support these requirements? (Select TWO).
A. 802.1X
B. RADIUS federation
C. WPS
D. Captive portal
E. WPA2
F. WDS
Which of the following can affect electrostatic discharge in a network operations center?
A. Fire suppression
B. Environmental monitoring
C. Proximity card access
D. Humidity controls
Management wants to ensure any sensitive data on company-provided cell phones is isolated in a single location that can be remotely wiped if the phone is lost. Which of the following technologies BEST meets this need?
A. Geofencing
B. Containerization
C. Device encryption
D. Sandboxing
A software development manager is taking over an existing software development project. The team currently suffers from poor communication due to a long delay between requirements documentation and feature delivery. This gap is resulting in an above average number of security- related bugs making it into production. Which of the following development methodologies is the team MOST likely using now?
A. Agile
B. Waterfall
C. Scrum
D. Spiral